2012 Recorded ICT Security Threats
By Brandon Teoh
This is going to be the most comprehensive summary of all ICT security threats that one can find online through 2012. This article attempts to identify all key threats which were discovered in 2012 and to perform analysis in terms of similarities and trends.
This report summarises data from a whole year perspective and is cross-vendor by compiling analysis and conclusions from different intelligence from vendors.
To begin with, it was all started with discovery of Koobface in Jan 2012.
Koobface
Jan 18 2012, Facebook identified five people as responsible for the Koobface worm; Anton Korotchenko, Alexander Koltyshev, Roman Koturbach, Syvatoslav Polinchuk, and Stanislav Avdeiko collectively known as the Koobface gang.
Koobface (an anagram of “Facebook”) spreads via social networking sites, infecting PCs and building a botnet of compromised computers. It is so sophisticated it can even create its own social networking accounts, so that it can aggressively post links helping it to spread further.
Koobface gang earned millions of dollars every year by compromising computers.
The Koobface worm is a sophisticated botnet uses a concept known as command & control (C & C) servers where botnets on infected computers will contact C&C servers for further instructions which changes according to dynamics. C&C servers get changes from time to time, thus leaving investigator with little trails for information.
It was reported to be able to hijack search queries to display advertisements.
Koobface worm works on Microsoft Windows, Mac and Linux.
Koobface was reported to make money through distribution of fake antivirus, click fraud, information-stealing malware, and online dating services.
OSX.FalshBack.K
OSX.Flashback is a Trojan horse that gathers information from the compromised computer.
It was started in late 2011.
It has come a long way from its humble beginnings as a social-engineering scam trying to pass off as a fake Flash update using digital certificates purporting to come from Apple. Flashback is now leveraging the latest Java vulnerability (BID 52161 – Oracle Java SE Remote Java Runtime Environment Denial Of Service Vulnerability ) in order to deliver its payload.
It is interesting to take note this time that the ultimate goal of the OSX.Flashback.K Trojan is to generate money through ad-clicking.
It works on the basis of command & control server; generating dynamic URLs as a form of reporting-back-to-the-HQ. These URLs are known as C & C (command and control) server addresses.
Once the HQ gained control of the infected PC, it will perform hijack on Google Ad-click.
This security threat makes a good case study for computer science and software engineering.
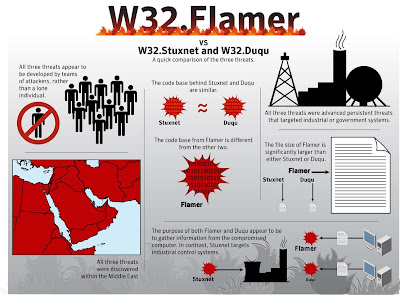
Flamer: The most complex malware threat since Stuxnet and Duqu
This malware was built with the ability to obtain information from infected systems primarily located in the Middle East.
It is found to be created by professionals and funded with directives.
The code includes multiple references to the string ‘FLAME’ which may be indicative of either instances of attacks by various parts of the code, or the malware’s development project name.
The threat has operated discreetly for at least two years with the ability to steal documents, take screenshots of users’ desktops, spread via USB drives, disable security vendor products, and under certain conditions spread to other systems. The threat may also have the ability to leverage multiple known and patched vulnerabilities in Microsoft Windows, in order to spread across a network.
It only targets Microsoft Windows.
Flamer also operates in the nature of command & control (C & C) similar to the likes of Kooface and etc.
Initial telemetry indicates that the targets of this threat are located primarily in Palestinian West Bank, Hungary, Iran, and Lebanon. Other targets include Russia, Austria, Hong Kong, and the United Arab Emirates. The industry sectors or affiliations of individuals targeted are currently unclear. However, initial evidence shows the victims may not all be targeted for the same reason. Many appear targeted for individual personal activities, rather than their company of employment. Interestingly, in addition to particular organisations being targeted, many of the attacked systems appear to be personal computers being used from home Internet connections.
Flamer was not found to reap monetory benefits for its creators except for cyber espionage. Instead, it was made to self-destruct after discovery.
Millions of LinkedIn Passwords Reportedly Leaked
On June 6, 2012, Sophos reported that A file containing 6,458,020 SHA-1 unsalted password hashes has been posted on the internet, and hackers are working together to crack them. On June 7, 2012, LinkedIn confirmed that it was legitimate.
Although the data did not include associated email addresses.
Salt, in computer security field, is a string that is added to your password before it is cryptographically hashed.It enables password lists be not able to be pre-computed based on dictionary attacks or similar techniques.
This is an important factor in slowing down people trying to brute force passwords. It buys time and unfortunately the hashes published from LinkedIn did not contain a salt.
To mitigate damage, LinkedIn immediately resolved this issue internally and emailed users to advise them to change new password immediately.
LinkedIn managed to resolved everything within 2 days of the incident even though this case has become a benchmark for bad computer security policy, control and implementation.
Android.Opfake
Android.Opfake is malware written for Android devices that masquerades as various apps and content, including even as an installer for the Opera Web browser and a pornographic movie, which requires the user to pay for them. It demands payment for the app or content through Short Message Service (SMS) messages.
Symantec found that it is being distributed as disguises for games such as Temple Run and Cut the Rope. The attackers have even gone so far as to include images of actual devices playing the games in an attempt to convince unsuspecting users that the malicious versions are actually legitimate.
‘Gauss’ – A New Complex Cyber-Threat Designed to Monitor Online Banking Accounts
Gauss is a complex, nation-state sponsored cyber-espionage toolkit designed to steal sensitive data, with a specific focus on browser passwords, online banking account credentials, cookies, and specific configurations of infected machines. It affected users mainly in the Middle East.
Gauss was discovered during the course of the ongoing effort initiated by the International Telecommunication Union (ITU), following the discovery of Flame. The effort is aimed at mitigating the risks posed by cyber-weapons, which is a key component in achieving the overall objective of global cyber-peace.
Gauss shares many similiarities with Flamer, these include These include similar architectural platforms, module structures, code bases and the usage of Command and Control servers (C & C Servers).
As the mater of fact, it was because of these similiarities which resulted in its detection in June 2012.
Since late May 2012, more than 2,500 infections were recorded by Kaspersky Lab’s cloud-based security system, with the estimated total number of victims of Gauss probably being in the tens of thousands. This number is lower compared to the case of Stuxnet but it’s significantly higher than the number of attacks in Flame and Duqu.
It is generally considered to be an online banking Trojan in which analysis shows it was designed to steal data from several Lebanese banks including the Bank of Beirut, EBLF, BlomBank, ByblosBank, FransaBank and Credit Libanais. In addition, it targets users of Citibank and PayPal.
Gauss got its name from the German mathematician Johann Carl Friedrich Gauss in which its creator named the main module. Other components bear the names of famous mathematicians as well, including Joseph-Louis Lagrange and Kurt Gödel.
Another key feature of Gauss is the ability to infect USB thumb drives, using the same LNK vulnerability that was previously used in Stuxnet and Flame. At the same time, the process of infecting USB sticks is more intelligent. Gauss is capable of “disinfecting” the drive under certain circumstances, and uses the removable media to store collected information in a hidden file. Another activity of the Trojan is the installation of a special font called Palida Narrow, and the purpose of this action is still unknown.
The investigation revealed that the first incidents with Gauss date back as early as September 2011. In July 2012 the command and control servers of Gauss stopped functioning.
More Recent Threats
Hurricane Sandy also wrecked havoc in mailboxes where spam emails related to Sandy was observed. The top word combinations in message headlines are “hurricane – sandy”, “coast – sandy”, “sandy – storm”, and “sandy – superstorm.” Intentions of these spam emails were typically to solicit illegal donations.
Offensive Facebook email leads to offensive Blackhole malware attacks were also discovered recently at which Facebook users are taunted with offensive comments with intentions of spreading links that lead to download of the notorious Blackhole exploit kit.
Kaspersky Lab is now supplying Facebook with up-to-the-minute data about the latest malicious software threats worldwide, which will be used to protect Facebook users from inadvertently visiting malicious web pages.
In addition to timely advice, Kaspersky Lab is also supplying Facebook users with an exclusive free six-month subscription for its popular consumer security products. This six-month offer allows users to download Kaspersky PURE Total Security and Kaspersky Security for Mac, ensuring they have the best protection on their machines.
Eugene Kaspersky, CEO and co-founder of Kaspersky Lab raised the bar on cyber-security threats. “In the long run, cyber-warfare is where all parties lose: attackers, victims and even uninvolved observers,” said Eugene during his keynote speech at the ITU Telecom World 2012 conference. He pointed out that the viable solution is via international cooperation and advanced technology as the key requirements to survive the age of cyber-warfare. Kaspersky cited that causes of events like the 2003 blackout in U.S. and Canada were results of both a software failure and an inability to monitor the real state of energy systems.
MiniFlame was discovered in Oct 2012 which analysts believed are behind the masterminds of Flammer and Gauss. Evidence reveals cooperation between the creators of Flame and Gauss, as both malicious programs can use miniFlame as a “plug-in” for their operations.
MiniFlame is also known as SPE and it shares same architectural platform as Flamer. As its name suggested, it can either run as standalone or as plug-in for Flamer.
Let’s hope that the world will have a peaceful Christmas for 2012.
Conclusion on common trends:
- Command and Control Server (C & C Server) – generation of dynamic URLs as a form of reporting-back-to-the–HQ for WORM propagation. These URLs are known as C & C (command and control) server addresses.
- Stuxnet and Duqu – The deadliest malware for 2012 was Flamer which analysts tend to compare it to Stuxnet (Discovered in June 2010) and Duqu (discovered on 1 September 2011) due to similarities.
All three (Flammer, Stuxnex, Duqu) were believed to be politically motivated and experts believe that they are responsible by completely different team of developers but share the same architecture (C & C Server) and functions but each target different purposes.
Stuxnex targets industrial system by first infecting on Windows platform and was particularly violent in Iran. Duqu targets Windows platform and was also rampant in Iran.
All three are WORM(s) where they are designed to replicate by themselves by leveraging on the concept of C & C Servers and they also come with Trojan ability. And all three targets Windows platform with Stuxnet and Duqu switched focus to targeting industrial systems.
The New York Times and The Washington Post reported that the masterminds behind Stuxnet, Duqu, and Flame — who Obama administration officials say were government technologists and intelligence officials from the U.S. and Israel.
- Malwares are increasingly adept at taking advantage of seasonal celebrations such as Halloween, Valentine’s day, Christmas, special occasions such as Olympics, Disasters to propagate security threats.
- Malware masterminds are coming to terms to common architectures and best practices almost as if they are part of a big family who operates underground operations. This is evident from the fact that the deadliest malwares such as Stuxnex, Duqu, Flammer and Gauss share technology similarities.
- The use of Web attack toolkits has grown significantly in the first half of 2012. Web Attack toolkits primarily focus on exploiting third-party browser plugins (which are out-of-date), such as Adobe Reader, Adobe Flash Player, and Java.
Web attack toolkits such as Blackhole accounts for almost two-thirds of all threat activity on malicious websites in 2011.
Based on data gathered in July 2012, there are currently three times as many Web attacks occurring now, as there where on average during the last half of 2011.
There are a variety of attack toolkits currently active; Blackhole, Phoenix, Nuclear Pack, Bleeding Life, and Eleonore are some of the more popular ones.
The reason for their popularity likely has to do with the versatility it offers attackers for compromising computers. No manual hacking is involved as the attack toolkit automates the exploit process.
- Malware Networks (Malnet)– distributed infrastructures within the Internet that are built, managed and maintained by cybercriminals for the purpose of launching a variety of attacks against unsuspecting users over extended periods of time.
A Malnet gathers users, typically when they are visiting trusted sites, and routes them to malware, via relay, exploit and payload servers that continually shift to new domains and locations.
The top 5 Malware networks are SHNAKULE, GOLMYN, CAVKA, NAARGO and CINBRIC. Shnakule is the most geographically dispersed of the five largest malnets with a presence in countries throughout Europe, the Middle East, Asia and the Americas.
It is most concentrated in the United States and Germany. Naargo is based in Israel, the Netherlands and Russia.
Shnakule is powered by drive-by downloads,fake AV,codecs, Flash and Firefox updates, botnet CnC controls, pornography, gambling, and work-at-home scams.
Traditional security defenses can’t protect businesses against sudden attacks from established malnet infrastructures. Instead of solutions that react to attacks as they occur – when damage has already been done – businesses need a defense that identifies and nullifies the sources of potential threats before they arrive.
You must be logged in to post a comment.



There are no comments
Add yours